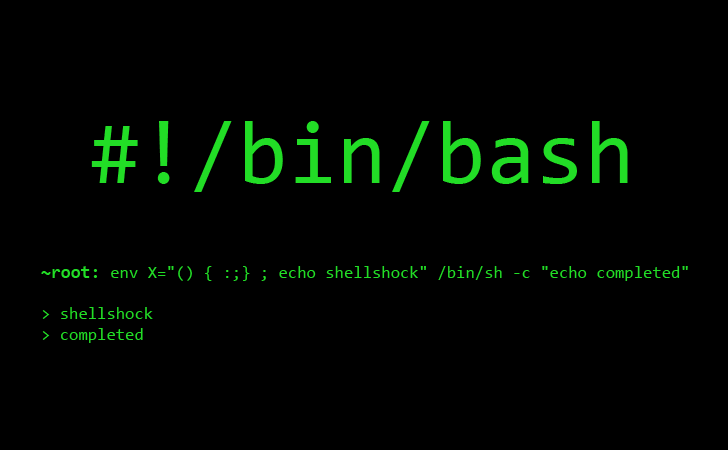
The majority of Linux based hosting servers generally use the BASH shell, or Bourne Again Shell. As such this is what we base most of our Linux server tutorials on. However other Linux shell’s exist, and it’s a good idea to make sure you know what Linux shell you’re using when you first login to […]
Category Archives: Linux Server Tutorials
The BASH Shell: Copy, Move & Delete Files on Linux Servers
Any webmaster will inevitably find themself staring at a terminal screen, tasked with a job of performing some management/maintenance work on a Linux based server. Most of the time you’ll find yourself doing basic tasks – like moving files, removing unnecessary directories, and renaming other ones. All of these things can be accomplished using a […]
How To Setup Linux on Amazon EC2 with Apache, PHP & MySQL
AWS is quickly turning into an extremely common solution – offering significantly more features than most VPS hosting providers, while also keeping the costs down. As such plenty of people aare turning to AWS for their online projects, starting from basic WordPress blogs – through to complex online applications. Through this tutorial we are going […]
Linux Server Tutorials
As a webmaster chances are you will wind up managing a Linux box or two in your time – and when you do you’ll be happy you learned these tricks. [divider3 text=”The Bash Shell”] How To Copy, Move, and Delete Files on Linux Servers A straightforward tutorial that should get you through most of the […]
Server Security: Processes and How to Terminate Them
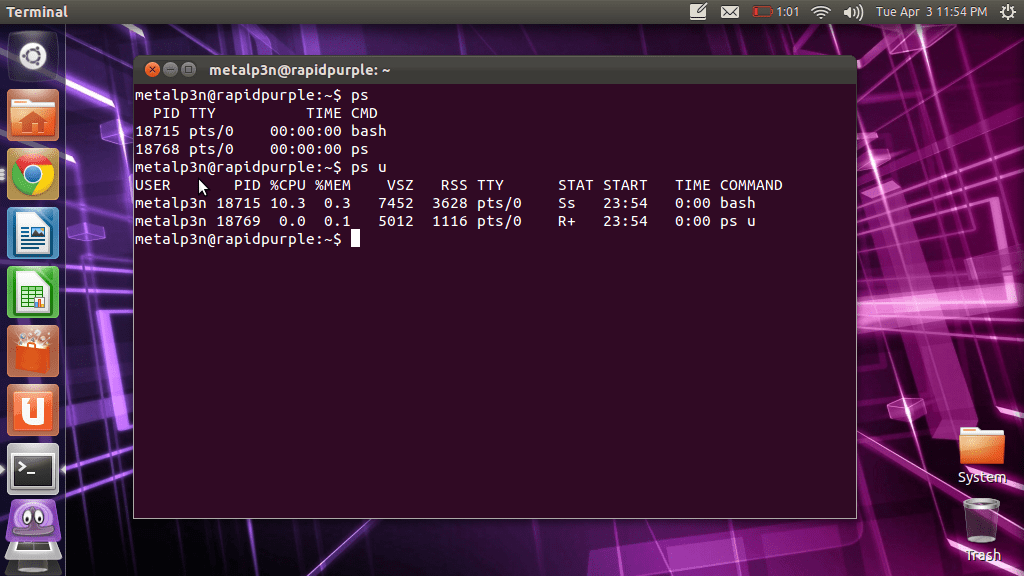
Since Linux is a multi-tasking system, in which many different programs or program threads may be running simultaneously, Linux keeps track of all individual tasks and processes – much like the Task Manager within Windows. Although these processes are usually well-behaved and well-managed by Linux itself – it’s always helpful to be able to know […]
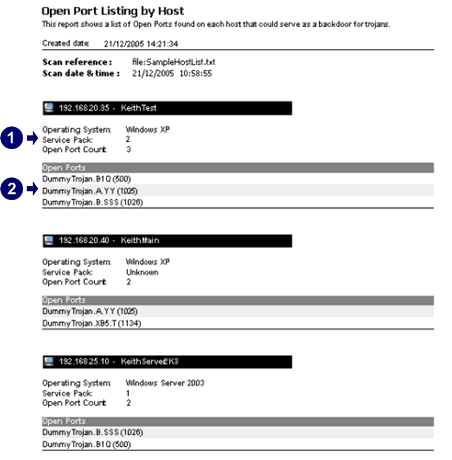
Trojan Port List
Following the recent breach of the popular hosting company, ServerPro, the internet is back to buzzing about trojans and server ports, which it should be. It never should have stopped in the first place. With that in mind – comes this list – listing the majority of the more popular known trojans, and the ports […]
Server Security: Turn Off rwhod
The rwhod daemon is a process that allows a remote user to see who is logged into your system. The client program is rwho. It has many of the same security problems as the finger daemon. For a crack,er use of rwho could allow him to watch for times on your system when nobody is […]
The BASH Shell: Pipelines
Pipelines are a great way to string together a series of commands. This means that the output from the first command in the pipeline is used as the input for the second command in the pipeline. The output from the second command in the pipeline is used as the input to the third command in […]
The BASH Shell: Command History & Aliases
Command History Bash keeps track of a certain number of previous commands that you have entered into the shell. The number of commands is given by a shell variable called HISTSIZE (which we will discuss later on). Bash stores the text of your previous commands in a history list. When you logon to to your […]
The BASH Shell: Wildcards & Command Line Completion
The GNU Bourne-Again SHell (BASH), as the name implies, is an extension of the Bourne shell. It provides a Command Line Interface (CLI) for working on *nix systems and is the most common shell used on Linux systems. Chances are that if you’re managing your own virtual or dedicated server – you’ll end up using […]