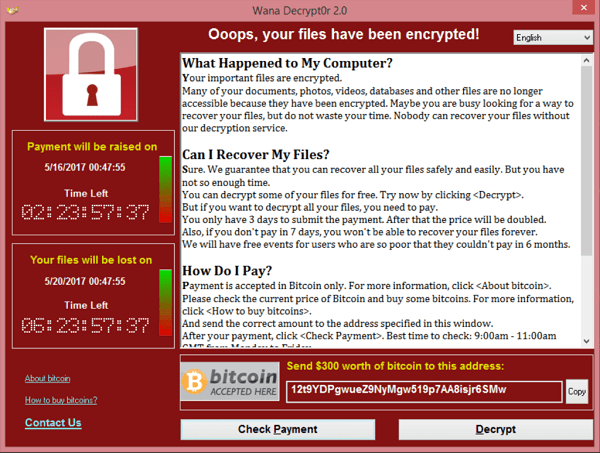
Last Friday the National Health Service in the United Kingdom reported outages as a massive malware attack brought down various computers and systems. As news of this broke, other organizations realized they were being hit by the same malware virus. Government bodies and individual users reported experiencing similar attacks. It quickly became obvious that the attacks, which were carried out by WannaCrypt, or WannaCry, were part of a larger, more coordinated effort. As the dust starts to settle on this attack, it’s important we all understand what actually happened & how we can protect ourselves – now and in the future.
What Did WannaCry/WannaCrypt Actually Do?
WannaCry is a type of ransomware. Once it infects your computer, it will take your files hostage by encrypting them. Once these files are encrypted it is very difficult to unlock them. WannaCry can decrypt them for you, but only if you pay up a ransom. The ransom starts at $300 and must be paid in bitcoin. It increases as time goes on.
In hindsight, it appears that the attacks didn’t start with the NHS, even if that’s what grabbed the most headlines, but instead Telefonica in Spain. From there, the malware quickly spread to the United Kingdom, Japan, the United States, Germany, Russia, and various other countries. It appears that in total at least 150 countries were hit. By the time the attack is fully measured don’t be surprised if every country reports infections.
Besides the NHS, other big targets included FedEx in the United States, the German railroad system Deutsche Bahn, the French automaker Renault, and even the Russian Interior Ministry. Such widespread attacks are not unheard of, but the speed at which it spread is remarkable.
Interestingly enough, it appears that the American National Security Agency (NSA) was not only aware of the vulnerability, but had actively developed tools to exploit it (DoublePulsar). While the investigation is on-going, it appears that leaked data and tools from the NSA may have actually been used to develop & launch the WannaCry attacks.
As of right now, it appears that Windows 10 was not hit by the WannaCry malware. If your Windows 10 operating system is up to date, you’re probably not at risk. That being said, vigilance is a must. So far, Windows 7, Windows Vista and several other operating systems appear unaffected, but you need to be especially careful if you are using one of these older systems. Users of older OS systems like Windows XP or Windows Server 2003 appear to be the main targets for these attacks – however Microsoft has released a critical patch for these, technically unsupported, operating systems.
Meanwhile, as the virus spread security experts around the world shifted focus to try and contain it, a computer expert operating under the name MalwareTech discovered that the WannaCry malware was communicating with an unregistered domain name. When s/he registered the domain, it set off a kill switch and stopped the malware dead in its tracks. This “accidental” hero may have possibly averted a much larger disaster. MalwareTech has since been doxed, so we ask that his privacy be maintained. Don’t punish the hero.
How to Stay Protected Against WannaCry/WannaCrypt
Now that the dust is clearing, security experts are warning people to update their computers and operating systems immediately. As it turns out – Microsoft released a critical patch back on March 14th 2017 to remove the underlying vulnerability exploited by WannaCry. If systems were up to date, they would have been protected from the attack. While many people and organizations like to delay updated security patches to ensure software compatibility, doing so leaves computers exposed. Leaving computers exposed leads us to situations like this.
Unfortunately new versions of WannaCry are already emerging and these don’t have easy kill switches. It seems likely that the malware is being launched by the same attackers as the original attack & currently it’s unclear if they have found a new weakness to exploit. Regardless any computer found to be infected with the WannaCry malware must be wiped and cleaned.
Everyone else should ensure that firewalls are up to date. Your using updated anti-virus software, and most importantly, make sure that your computer operating system is up to date on the most recent patches. Taking these steps will help you mitigate the existing risks. If you or your company works in a sensitive industry, such as health care, it is especially important to make sure you are up to date, and make sure you have a safe backup to restore to – you never know.