Surely you’ve heard the term Shellshock exploit be mentioned everyone across the internet these last couple of days, however what is it exactly and what does it really mean for you? Well, Shellshock is the name for a brand new exploit which targets a vulnerability in Bash. Bash, an acronym for Bourne Again Shell, is a command-line shell used by many UNIX computers. In-fact I feature several tutorials regarding working with Bash here. UNIX is an operating system on which many others are built, such as Linux and Mac OS. So if your utilizing a Linux based web server for your website, or a Mac OS computer at the office – your system could very well be vulnerable.
Bash is a key component of the web servers that run at least half of the websites on the internet, in-fact your probably running your very own website on a Linux based server utilizing Bash. Even if you don’t use any aspect of Linux yourself, a huge proportion of the Internet runs on the “backbone” of Apache, which uses Bash heavily. Bash is also used in the background by web browsers, email apps, FTP (website upload) apps and all kinds of other applications. One way or another you are, or you have, used the Bash shell.
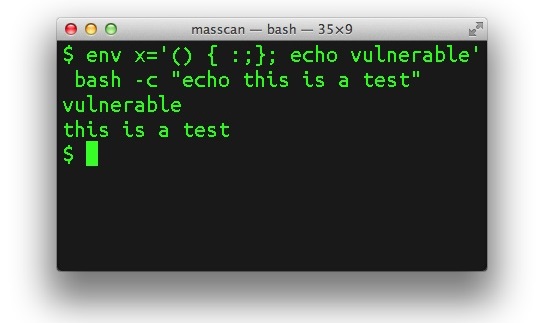
So what exactly does Shellshock do? Shellshock allows anyone to run any program via text commands through the use of Bash, or Terminal as you’re used to calling it in Mac OS. That means one can run key-logging software, steal personal information, etc. There’s an even bigger problem to Shellshock however. Every single version of Bash up to 4.3 is vulnerable – and that leaves ALOT of patching to be done.
Patches for the main bug – designated CVE-2014-6271 – are available for most Linux distributions. However, there are reports that the patch is NOT a complete fix and so a further vulnerability, CVE-2014-7169, is being tracked. Fixes against this second vulnerability have not yet been widely distributed.
Apple is also hard at work patching MAC OS – however there is some good news for Apple owners. There is a chance you may not be vulnerable at all. With OS X, systems are safe by default and not exposed to remote exploits of bash unless users configure advanced UNIX services. So long as you’ve never configured those services – you’re good to go. If you have however – Apple is working on a fix for you – right along with figuring out how to make your phone not bend in your back pocket.